If you want to continue working on kernel development while on a staycation or traveling for other reasons, you need to securely access your home lab. After considering several open source solutions including WireGuard, I have settled down to use Tailscale VPN for my home lab. It is simple, fast and easy to maintain. Most importantly, it works on all architectures I use in my home lab. This post is a quick guide to my VPN setup.
Tailscale is a zero-config VPN built on WireGuard. The most likeable feature is its simplicity. There is hardly anything configuration needed and it works with all the devices in my home lab (ARM, RISC-V, amd64) running different Linux distributions.
In Tailscale VPN, each system is a node of the same VPN network. The co-ordination and management of the tunnels are done by a co-ordination server hosted in public cloud by Tailscale. The data plane is point-to-point mesh between the nodes, so it is scalable and fast.
To get started, log into https://login.tailscale.com/start and create your Tailscale account. You can use an identity provider like github for this as well. From the “Machines” tab of the Tainscale login dashboard, you can add devices using the “Add device” button. Typically it will show the instructions on how to add a device by installing the necessary software on it.
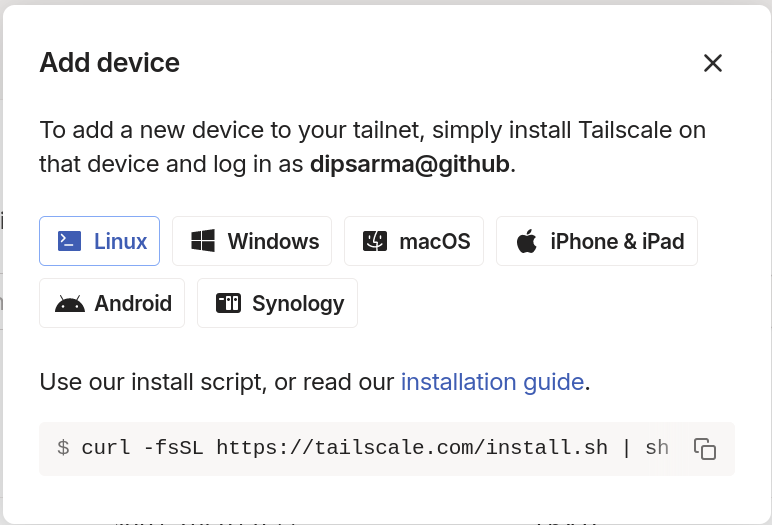
The tailscale software is very portable – I have been able to add ARM, RISCV and amd64 Linux systems into my Tailscale VPN network using the above instructions.
user@rv-vf2-1:~$ sudo curl -fsSL https://tailscale.com/install.sh | sh
Installing Tailscale for debian bookworm, using method apt
+ sudo mkdir -p --mode=0755 /usr/share/keyrings
+ curl -fsSL https://pkgs.tailscale.com/stable/debian/bookworm.noarmor.gpg
+ sudo tee /usr/share/keyrings/tailscale-archive-keyring.gpg
+ curl -fsSL https://pkgs.tailscale.com/stable/debian/bookworm.tailscale-keyring.list
+ sudo tee /etc/apt/sources.list.d/tailscale.list
# Tailscale packages for debian bookworm
deb [signed-by=/usr/share/keyrings/tailscale-archive-keyring.gpg] https://pkgs.tailscale.com/stable/debian bookworm main
+ sudo apt-get update
Hit:1 https://snapshot.debian.org/archive/debian-ports/20221225T084846Z unstable InRelease
Err:1 https://snapshot.debian.org/archive/debian-ports/20221225T084846Z unstable InRelease
The following signatures were invalid: EXPKEYSIG E852514F5DF312F6 Debian Ports Archive Automatic Signing Key (2022) <ftpmaster@ports-master.debian.org>
Get:2 https://pkgs.tailscale.com/stable/debian bookworm InRelease
Get:3 https://pkgs.tailscale.com/stable/debian bookworm/main all Packages [354 B]
Get:4 https://pkgs.tailscale.com/stable/debian bookworm/main riscv64 Packages [7258 B]
Fetched 14.2 kB in 2s (6473 B/s)
Reading package lists... Done
W: An error occurred during the signature verification. The repository is not updated and the previous index files will be used. GPG error: https://snapshot.debian.org/archive/debian-ports/20221225T084846Z unstable InRelease: The following signatures were invalid: EXPKEYSIG E852514F5DF312F6 Debian Ports Archive Automatic Signing Key (2022) <ftpmaster@ports-master.debian.org>
W: Failed to fetch https://snapshot.debian.org/archive/debian-ports/20221225T084846Z/dists/unstable/InRelease The following signatures were invalid: EXPKEYSIG E852514F5DF312F6 Debian Ports Archive Automatic Signing Key (2022) <ftpmaster@ports-master.debian.org>
W: Some index files failed to download. They have been ignored, or old ones used instead.
+ sudo apt-get install -y tailscale tailscale-archive-keyring
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
The following additional packages will be installed:
iptables libip6tc2
Suggested packages:
firewalld
The following NEW packages will be installed:
iptables libip6tc2 tailscale tailscale-archive-keyring
0 upgraded, 4 newly installed, 0 to remove and 1 not upgraded.
Need to get 26.3 MB of archives.
After this operation, 50.3 MB of additional disk space will be used.
Get:1 https://snapshot.debian.org/archive/debian-ports/20221225T084846Z unstable/main riscv64 libip6tc2 riscv64 1.8.8-1 [33.7 kB]
Get:3 https://pkgs.tailscale.com/stable/debian bookworm/main all tailscale-archive-keyring all 1.35.181 [3082 B]
Get:2 https://pkgs.tailscale.com/stable/debian bookworm/main riscv64 tailscale riscv64 1.62.1 [25.9 MB]
Get:4 https://snapshot.debian.org/archive/debian-ports/20221225T084846Z unstable/main riscv64 iptables riscv64 1.8.8-1 [348 kB]
Fetched 26.3 MB in 6s (4121 kB/s)
Selecting previously unselected package libip6tc2:riscv64.
(Reading database ... 76920 files and directories currently installed.)
Preparing to unpack .../libip6tc2_1.8.8-1_riscv64.deb ...
Unpacking libip6tc2:riscv64 (1.8.8-1) ...
Selecting previously unselected package iptables.
Preparing to unpack .../iptables_1.8.8-1_riscv64.deb ...
Unpacking iptables (1.8.8-1) ...
Selecting previously unselected package tailscale.
Preparing to unpack .../tailscale_1.62.1_riscv64.deb ...
Unpacking tailscale (1.62.1) ...
Selecting previously unselected package tailscale-archive-keyring.
Preparing to unpack .../tailscale-archive-keyring_1.35.181_all.deb ...
Unpacking tailscale-archive-keyring (1.35.181) ...
Setting up tailscale-archive-keyring (1.35.181) ...
Setting up libip6tc2:riscv64 (1.8.8-1) ...
Setting up iptables (1.8.8-1) ...
update-alternatives: using /usr/sbin/iptables-legacy to provide /usr/sbin/iptables (iptables) in auto mode
update-alternatives: using /usr/sbin/ip6tables-legacy to provide /usr/sbin/ip6tables (ip6tables) in auto mode
update-alternatives: using /usr/sbin/iptables-nft to provide /usr/sbin/iptables (iptables) in auto mode
update-alternatives: using /usr/sbin/ip6tables-nft to provide /usr/sbin/ip6tables (ip6tables) in auto mode
update-alternatives: using /usr/sbin/arptables-nft to provide /usr/sbin/arptables (arptables) in auto mode
update-alternatives: using /usr/sbin/ebtables-nft to provide /usr/sbin/ebtables (ebtables) in auto mode
Setting up tailscale (1.62.1) ...
Created symlink /etc/systemd/system/multi-user.target.wants/tailscaled.service → /lib/systemd/system/tailscaled.service.
Processing triggers for man-db (2.11.1-1) ...
Processing triggers for libc-bin (2.36-6) ...
+ [ false = true ]
+ set +x
Installation complete! Log in to start using Tailscale by running:
sudo tailscale up
Once the node software is installed (see above), you can start the VPN to add it to your tailscale network by executing sudo tailscale up. This command will prompt you for your Tailscale credentials. I use github credentials in Tailscale, so when prompted, I use my github credentials to log in from the node. Once that is done, the machine shows up in your private Tailscale network.
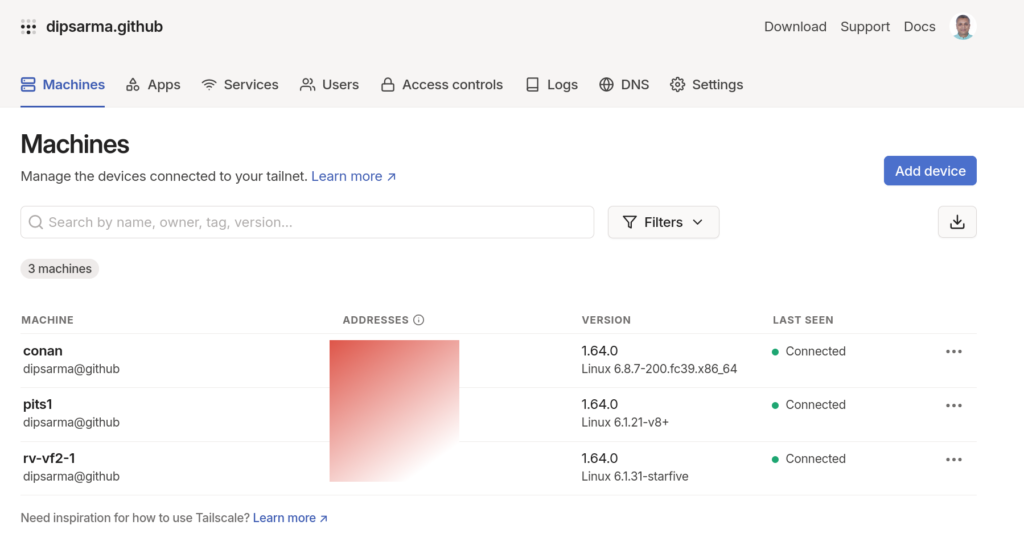
Once all the systems are added to the tailscale network, you can see a dashboard like above in https://login.tailscale.com. Tailscale also provides DNS service, so you can connect to any of your home lab machines in the VPN network using host names listed in the Addresses section (blurred out above) the Machines tab.
